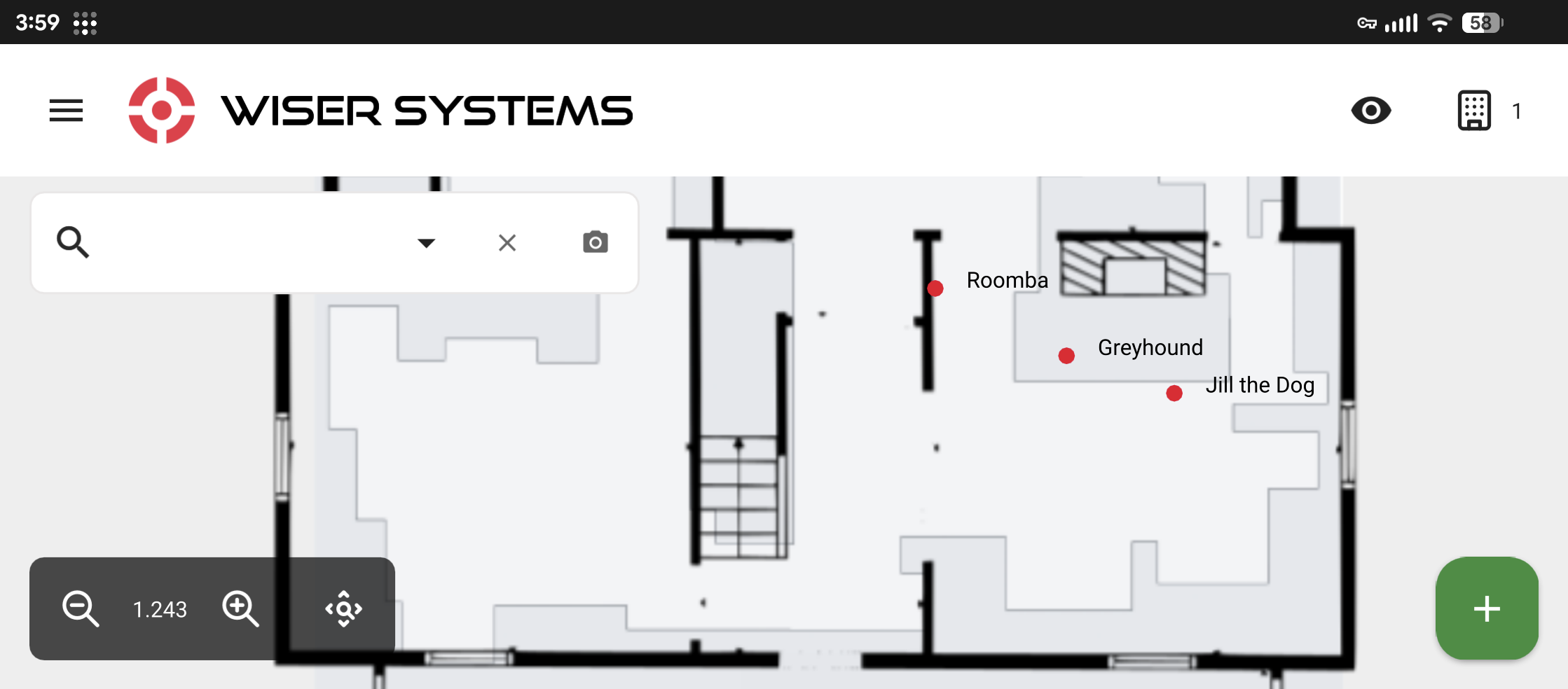
The WISER solution can easily and accurately locate tens of thousands of tagged items across a million square feet of facility. But I want to tell you how I use it to remotely check on my cats and dogs at home. As an excuse to talk about networking.


As a WISER engineer, I run a small tracking mesh at home for development work, and it is useful to have tags that move around on their own. The pets are honorary test engineers. But the system is too useful not to use personally. For example, I have Home Assistant using the WISER API to start the Roomba when the dogs are out of the house. I also have the WISER App installed on my phone so I can tell the cat sitter where to find the cats while we are traveling. But this requires the WISER server to be accessible from outside the local network.
Each area tracked by WISER’s solution is mediated by a single central server that aggregates data from multiple on-site tags and, in turn, is managed by multiple users and API integrations. Users may want to manage that data remotely or use the WISER App off-site. The computer hosting the server may be in a different facility or the cloud. This means hardware devices, users, and integrations may be at different physical locations and on different networks. In this article, we will walk through one lightweight method of bridging them together.
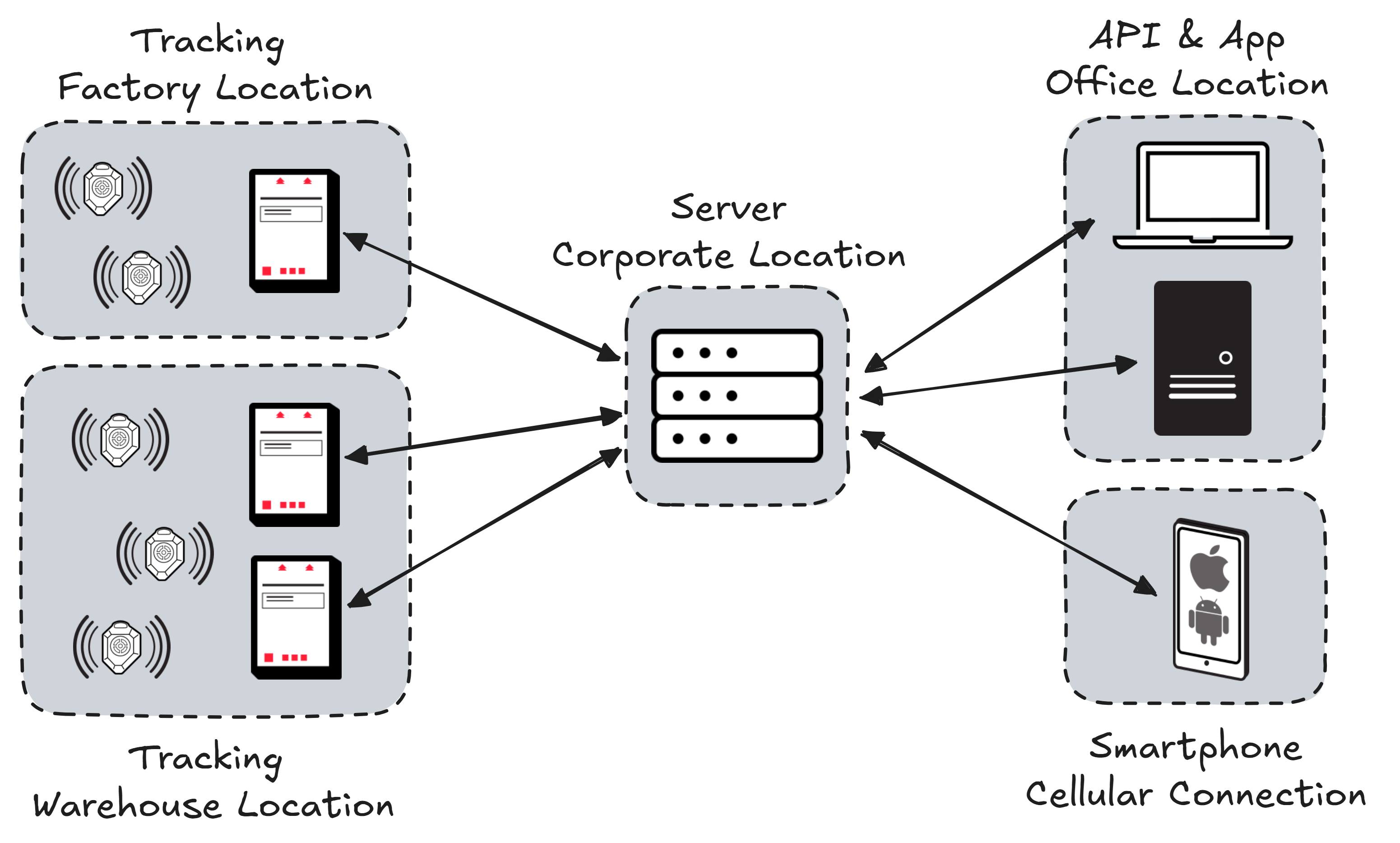
It may be tempting to simply make the server available on the internet. After all, WISER’s server has no known security vulnerabilities. But that brings us to our first Public Service Announcement.
Never connect a service to the internet unless internet connectivity is that service’s only purpose.
Only services like websites, email servers, and traditional VPNs should be open to the internet. That does not include any WISER product. If you are running a remote desktop tool open to the wide internet, I am talking to you. The first layer of authentication and encryption in defense against the internet should be provided by a service that has been purpose-built and battle-tested by many users over many years.
VPNs are a great solution. Larger corporations likely already manage connections between sites and provide a remote VPN onto the company network. But my home network does not have a corporate VPN. At WISER, we are big fans of Tailscale because it magically handles most complex network configurations with minimal setup. Although it functions like a VPN at first glance, there are significant differences under the hood.
Tailscale is not itself an identity provider; you cannot log into Tailscale. Instead, we choose a trusted single-sign-on (SSO) provider like Apple, Google, or Microsoft (or your corporation’s). Download, install, and sign in to Tailscale on the WISER Server’s computer and any remote devices following Tailscale’s excellent Getting Started documentation. Additional users can then be invited into the Tailscale network.
Tailscale is a mesh network, and connections are directly peer-to-peer. Both ends open outbound connections to Tailscale’s coordination server first to rendezvous with each other. As long as both ends can access the internet somehow, they can open an encrypted tunnel to each other. Rather than connecting to a VPN server, you authenticate devices with this provider. Tailscale manages the encryption keys, allowing any device to connect to any other device.
A quick tangent, services like Shodan.io constantly scrape the internet to catalog the listening ports of everything from VPNs and email servers to security cameras and door locks. When a security vulnerability is discovered in one of them, a bad actor can simply go down the list, breaking into them. I could run an internet-facing VPN server from my home, but it would be accessible to every country in the world. Unless I am as vigilant about updates as an IT professional, that is a risk. Tailscale moves that exposed listening port to a professionally managed coordination server somewhere else, and my home network remains invisible.
Returning to Tailscale, and then… well that’s it, these devices are now connected as if they were plugged into the same network. If I log into the Tailscale Admin Console in a web browser, click on the Windows system tray icon, or open the smartphone app, I can see all the devices connected and their IP addresses on my Tailscale network.
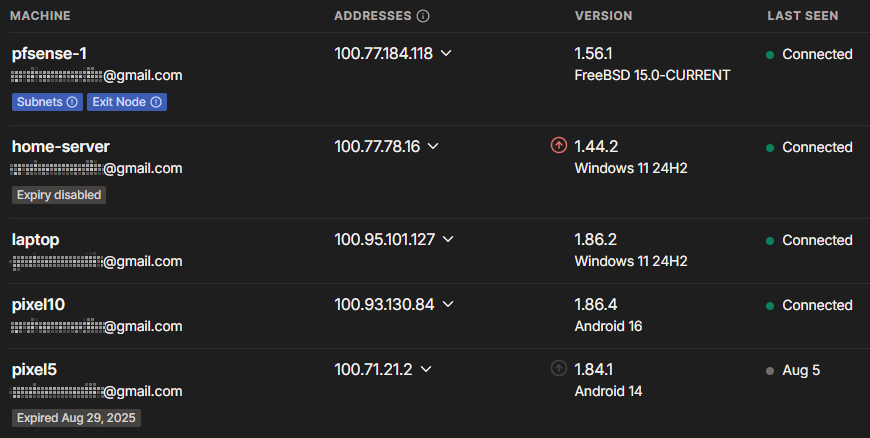
Tailscale uses a special range of 100.x.y.z addresses to avoid conflicts with other local network addresses. I can show you these because the Tailscale addresses are not accessible to the internet any more than your other local network addresses.
At this point we could type that 100.x.y.z server address into the WISER App or API integration, but Tailscale provides another great feature, MagicDNS. MagicDNS is magic because it just works, and DNS is also magic because it lets us ignore IP addresses and networking details in favor of human-readable names. If the server moves, or the network changes, this name will continue to work.
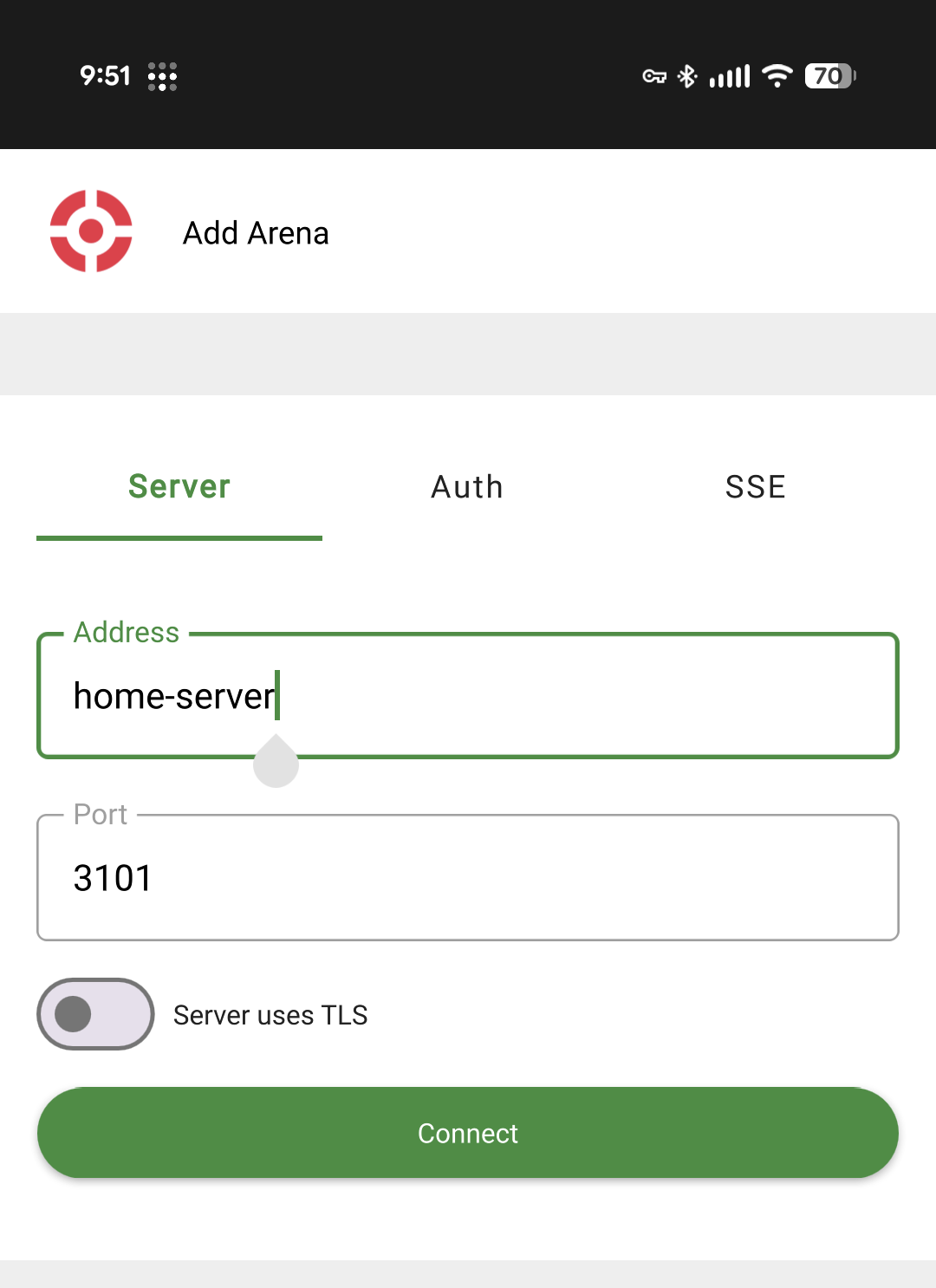
If we want to place the WISER server at a different location or network than the WISER tracking mesh, we have one more hoop to jump through. WISER Mesh Hubs are the devices that connect the WISER Antennas to the local network and the WISER server, but they themselves are not capable of running Tailscale. We need some other computer or device on the same network as the Mesh Hubs to be the Tailscale connection gateway. This Tailscale gateway could be anything that supports Tailscale, like a PC, virtual machine, or managed network switch. (A Raspberry Pi works well)
We set up that Tailscale gateway just as before. However, we have a problem, in that by design the WISER server can only access that Tailscalse gateway device, not the rest of the network that includes the Mesh Hubs. One solution to this is to use Tailscale’s subnets feature, which opens some of that Tailscale gateway’s local network to the Tailscale network. (Tailscale Exit Nodes are different. They redirect all traffic, more like a traditional VPN.) Follow the steps in Tailscale’s Configure a subnet router guide to allow routing to the range of IPs that include the Mesh Hubs. The WISER server can then access the Mesh Hubs as if the server were on the same local network.
My WISER hardware is connected to my home router which is also my Tailscale gateway to the Tailscale network, so when I moved to a new house and packed up my computer, I copied my WISER server over to a free-tier AWS cloud server, changed the Tailscale name, and everything continued to work seamlessly. When I got my home computer set back up, it took seconds to swap back. Because Tailscale links devices together as if they were all on the same local network, the sky is the limit here. WISER data can be accessed from anywhere.
If you are interested in talking with someone from WISER about how we can help at your facility, please feel free to reach out. You can contact us via our website, email, or phone.